 |
 |
Assignment
Date: 2/22/2012
Due Day: 2/29/2012 (revised)
Related documents:
Description:
Logistics:
| Name | rs1 | rs2 | rs3 | vip | dip |
|---|---|---|---|---|---|
| Ahmad, Adil Mohammed | 128.198.50.136 | 128.198.50.137 | 128.198.50.138 | 128.198.50.139 | 128.198.50.140 |
| Ahmed, Mohammed | 128.198.50.141 | 128.198.50.142 | 128.198.50.143 | 128.198.50.144 | 128.198.50.145 |
| Altarouti, Feras Ali | 128.198.50.146 | 128.198.50.147 | 128.198.50.148 | 128.198.50.149 | 128.198.50.150 |
| Albahdal, Abdullah Abdulaziz | 128.198.50.151 | 128.198.50.152 | 128.198.50.153 | 128.198.50.154 | 128.198.50.155 |
| Alcorn, Joshua | 128.198.50.156 | 128.198.50.157 | 128.198.50.158 | 128.198.50.159 | 128.198.50.160 |
| Alharthi, Ahmed | 128.198.50.161 | 128.198.50.162 | 128.198.50.163 | 128.198.50.164 | 128.198.50.165 |
| Alkaoud, Hessah Hassan | 128.198.50.166 | 128.198.50.167 | 128.198.50.168 | 128.198.50.169 | 128.198.50.170 |
| Almutawa, Ammar Hussain | 128.198.50.171 | 128.198.50.172 | 128.198.50.173 | 128.198.50.174 | 128.198.50.175 |
| Alsaadi, Fawaz Eid | 128.198.50.176 | 128.198.50.177 | 128.198.50.178 | 128.198.50.179 | 128.198.50.180 |
| Alsahafi, Abdulrhman I | 128.198.50.181 | 128.198.50.182 | 128.198.50.183 | 128.198.50.184 | 128.198.50.185 |
| Alsolami, Fahad Jazi | 128.198.50.186 | 128.198.50.187 | 128.198.50.188 | 128.198.50.189 | 128.198.50.190 |
| Alzahrani, Hamdan | 128.198.50.195 | 128.198.50.196 | 128.198.50.197 | 128.198.50.198 | 128.198.50.199 |
| Alzahrani, Omar J | 128.198.50.200 | 128.198.50.201 | 128.198.50.202 | 128.198.50.203 | 128.198.50.204 |
| Anvesh, Raavi | 128.198.50.205 | 128.198.50.206 | 128.198.50.207 | 128.198.50.208 | 128.198.50.209 |
| Ayodele, Anthony Ojo | 128.198.50.210 | 128.198.50.211 | 128.198.50.212 | 128.198.50.213 | 128.198.50.214 |
| Best, Adam | 128.198.50.215 | 128.198.50.216 | 128.198.50.217 | 128.198.50.218 | 128.198.50.219 |
| Brachfeld, Lawrence Jay | 128.198.50.220 | 128.198.50.221 | 128.198.50.222 | 128.198.50.223 | 128.198.50.224 |
| Cheng, Dazhao | 128.198.50.225 | 128.198.50.226 | 128.198.50.227 | 128.198.50.228 | 128.198.50.229 |
| Gilbert, Sampson | 128.198.50.230 | 128.198.50.231 | 128.198.50.232 | 128.198.50.233 | 128.198.50.234 |
| Hanson, Cody Lawrence | 128.198.50.235 | 128.198.50.236 | 128.198.50.237 | 128.198.50.238 | 128.198.50.239 |
| Hofflander, Brian James | 128.198.50.240 | 128.198.50.241 | 128.198.50.242 | 128.198.50.243 | 128.198.50.244 |
| Kateb, Faris A | 128.198.50.245 | 128.198.50.246 | 128.198.50.247 | 128.198.50.248 | 128.198.50.249 |
| Kretschmer, William C | 128.198.50.250 | 128.198.50.251 | 128.198.50.252 | 128.198.50.253 | 128.198.50.254 |
| Lykins, Rodney D | 128.198.49.67 | 128.198.49.68 | 128.198.49.69 | 128.198.49.70 | 128.198.49.71 |
| Nash, Berck Erin | 128.198.49.72 | 128.198.49.73 | 128.198.49.74 | 128.198.49.75 | 128.198.49.76 |
| Nesterenko, Matthew Alexander | 128.198.49.77 | 128.198.49.78 | 128.198.49.79 | 128.198.49.80 | 128.198.49.81 |
| Odell, Craig James | 128.198.49.82 | 128.198.49.83 | 128.198.49.84 | 128.198.49.85 | 128.198.49.86 |
| Omar, El Shibani | 128.198.49.87 | 128.198.49.88 | 128.198.49.89 | 128.198.49.90 | 128.198.49.91 |
| Rajagopal, Suresh | 128.198.49.92 | 128.198.49.93 | 128.198.49.94 | 128.198.49.95 | 128.198.49.96 |
| Ravikumar, Roshnee | 128.198.49.97 | 128.198.49.98 | 128.198.49.99 | 128.198.49.100 | 128.198.49.101 |
| Tedla, Suneetha | 128.198.49.102 | 128.198.49.103 | 128.198.49.104 | 128.198.49.105 | 128.198.49.106 |
| Zhao, Rui | 128.198.49.107 | 128.198.49.108 | 128.198.49.109 | 128.198.49.110 | 128.198.49.111 |
| createClassIPAssignmentCS526.pl |
[root@gandalf named]# nslookup abestvip.csnet.uccs.edu Server: 128.198.1.250 Address: 128.198.1.250#53 Non-authoritative answer: Name: abestvip.csnet.uccs.edu Address: 128.198.50.218
Network |
Vlan |
Description |
Gateway |
Host Start |
Host End |
Broadcast |
NETMASK |
128.198.50.128/26 |
Vlan 507 |
Class1 |
.50.129 |
.50.131 |
.50.190 |
.50.191 |
255.255.255.192 |
128.198.50.192/26 |
Vlan 508 |
Class2 |
.50.193 |
.50.195 |
.50.254 |
.50.255 |
255.255.255.192 |
128.198.49.64/26 |
Vlan 492 |
Class 3 |
.49.65 |
.49.67 |
.49.126 |
.49.127 |
255.255.255.192 |
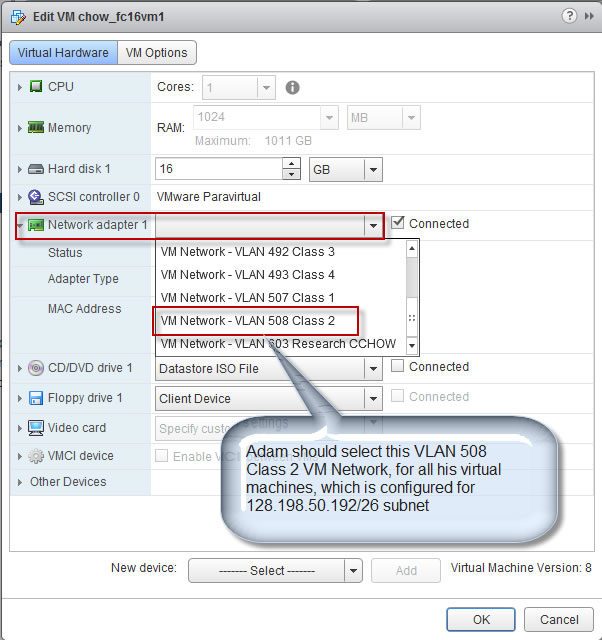
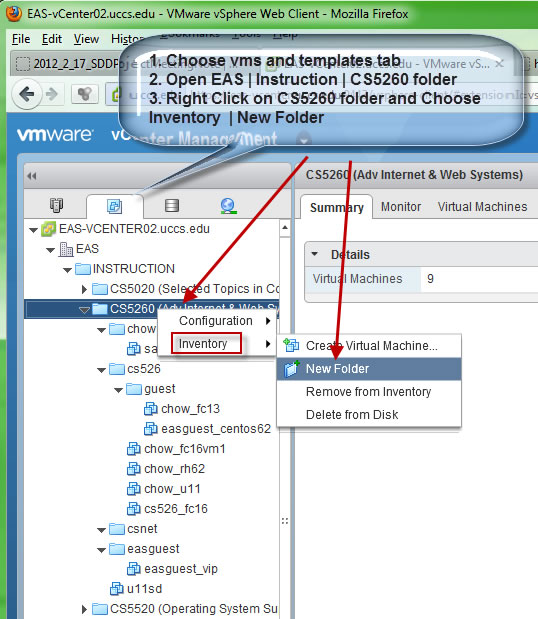
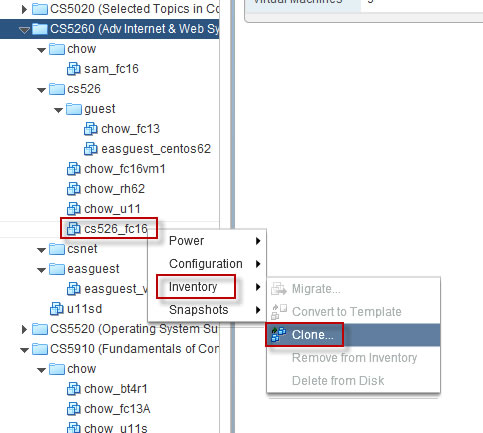
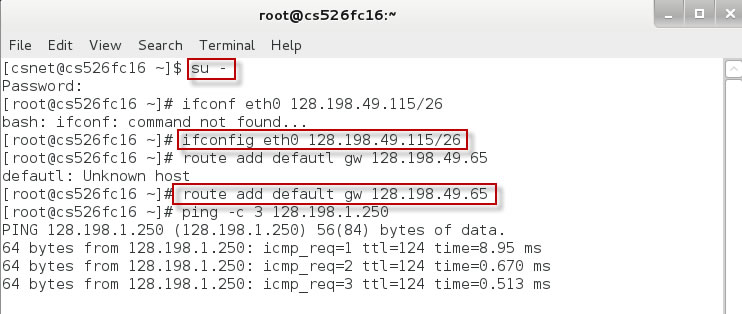
Part 1. Create a folder and clone/configure a FC16 virtual machine.
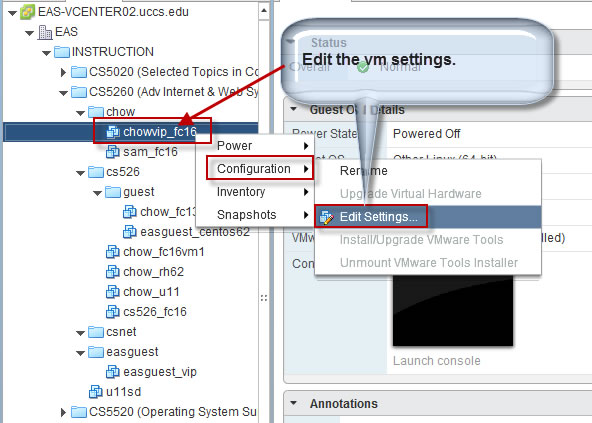
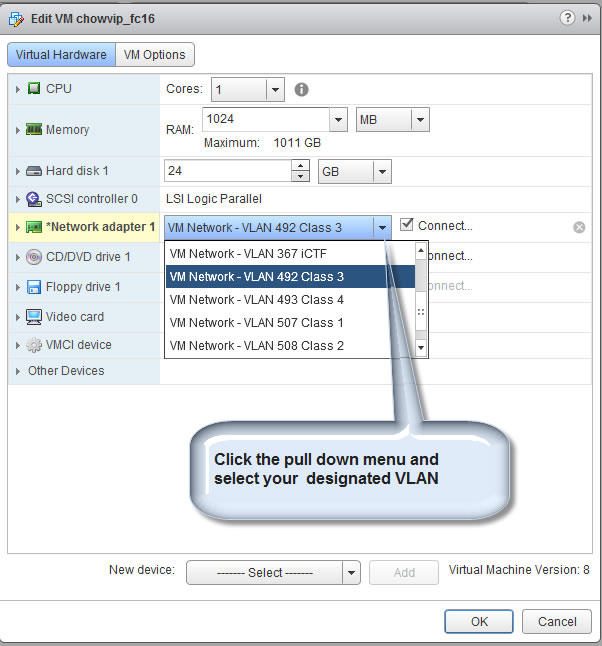
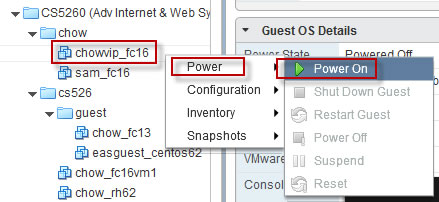
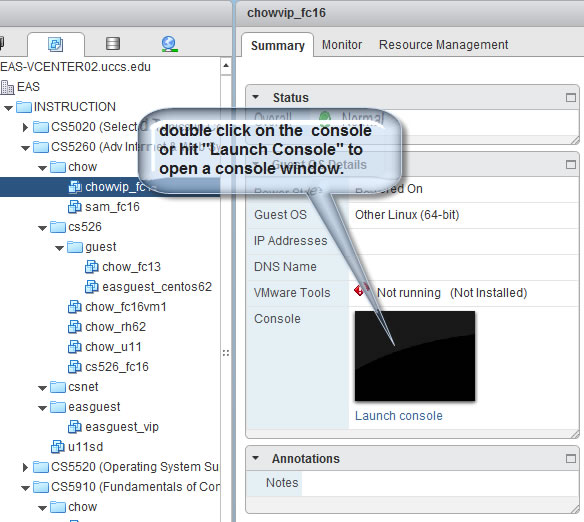
Part 3. Create Password Protected Web Directory and Explore Apache .htaccess access control
Exercise A:
AuthType Basic
AuthName cs526realm
AuthUserFile /var/www/apacheticket
require ceo, manager, staff
Exercise B:
Questions.
Create a homework web page hw3.html in your cs526 personal web page directory. Email the url and anawers of the above questions to cchow@uccs.edu and aalmuray@uccs.edu with subject field "CS526 hw3".