We have setup Make sure you suspend the virtual machines each time you finish your experiment.
Configure network interfaces of the virtual machine
# line, and change only the value of the NAME= key.
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:d2:b9:bc", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth0"
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:42:4e:8d", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth1"
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:42:4e:83", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth2"
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:42:4e:97", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth3"
By examining the configuration of network adpator 1 (click Network Aadpator 1 icon on the summary tab of chow_FWout), 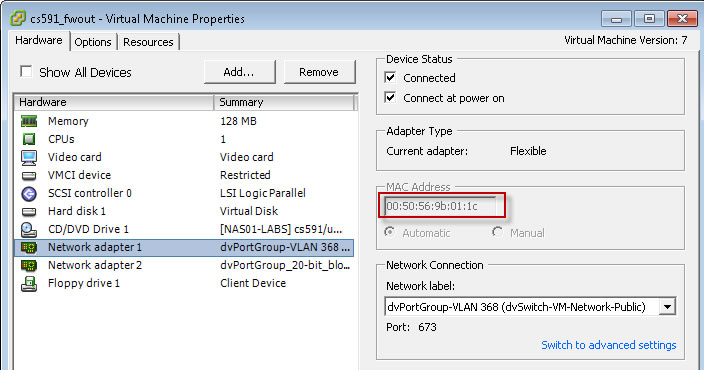
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:42:4e:83", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth2"
to
# PCI device 0x1022:0x2000 (pcnet32)
SUBSYSTEM=="net", ACTION=="add", DRIVERS=="?*", ATTR{address}=="00:0c:29:42:4e:83", ATTR{dev_id}=="0x0", ATTR{type}=="1", KERNEL=="eth*", NAME="eth0"
similar we can map mac address of the network adapter 2
to eth1, and that of network adapter 3 to eth2.
once the /etc/udev/rules.d/70-persistent-net.rules is edited, reboot the machine. You should
eth0, eth1, and eth2 map properly to network adapter 1, 2, and 3.
csnet@beta:~$ sudo bash
[sudo] password for csnet:
root@beta:~# ifconfig -a
eth0 Link encap:Ethernet HWaddr 00:0c:29:1a:45:34
BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:117 errors:0 dropped:0 overruns:0 frame:0
TX packets:79 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:15202 (14.8 KB) TX bytes:8988 (8.7 KB)
Interrupt:16 Base address:0x1400
eth1 Link encap:Ethernet HWaddr 00:0c:29:1a:45:34
BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:18 Base address:0x1800
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:90 errors:0 dropped:0 overruns:0 frame:0
TX packets:90 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:10260 (10.0 KB) TX bytes:10260 (10.0 KB)
root@beta:~# ifconfig eth1 172.16.212.1 netmask 255.255.255.0 root@beta:~# ifconfig eth0 128.198.161.212 netmask 255.255.255.224 root@beta:~# ifconfig eth0:1 128.198.161.213/27 root@beta:~# route add default gw 128.198.161.193 root@beta:~# netstat -rn Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface 128.198.161.192 0.0.0.0 255.255.255.224 U 0 0 0 eth0 172.16.212.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1 0.0.0.0 128.198.161.193 0.0.0.0 UG 0 0 0 eth0
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
#iface eth0 inet dhcp
auto eth0
iface eth0 inet static
address 128.198.161.212
netmask 255.255.255.224
gateway 128.198.161.193
auto eth0:1
iface eth0:1 inet static
address 128.198.161.213
netmask 255.255.255.224
# eth1
auto eth1
iface eth1 inet static
address 172.16.212.1
netmask 255.255.255.0
root@c591_fwin:~# cat /proc/sys/net/ipv4/ip_forward
1
root@cs591_ufw2:~# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
172.16.212.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
10.0.212.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
0.0.0.0 172.16.212.1 0.0.0.0 UG 0 0 0 eth0
# Advanced Micro Devices [AMD] 79c970 [PCnet32 LANCE]
DEVICE=eth0
#BOOTPROTO=dhcp
ONBOOT=yes
NM_CONTROLLED=no
BOOTPROTO=static
NETMASK=255.255.255.0
IPADDR=172.16.212.2
GATEWAY=172.16.212.1
TYPE=Ethernet
USERCTL=no
PEERDNS=yes
IPV6INIT=no
# Do not remove the following line, or various programs
# that require network functionality will fail.
#127.0.0.1 fc22.csnet.uccs.edu fc11 localhost.localdomain localhost localhost
172.16.212.2 cs591.csnet.uccs.edu cs591 localhost.localdomain localhost localhost
::1 localhost6.localdomain6 localhost6
You should satisfy the httpd.
root@rwhite2_fc9 ~]# service httpd restart
Stopping httpd: [FAILED]
Starting httpd: [ OK ]
Message: Access denied with code 400 (phase 2). Pattern match "^[\\d\\.]+$" at REQUEST_HEADERS:Host. [id "960017"] [msg "Host header is a numeric IP address"] [severity "CRITICAL"]
Action: Intercepted (phase 2)
Stopwatch: 1227281695740933 1332 (685 1003 -)
Producer: ModSecurity v2.1.6 (Apache 2.x)
Server: Apache/2.2.8 (Fedora)
iptables -P INPUT DROP iptables -P OUTPUT DROP iptables -P FORWARD DROP
iptables -A FORWARD -i ____ -m state --state NEW -j LOG --log-prefix "DMZ-intra Violation iptables -A FORWARD -i ____ -m state --state NEW -j DROP
Find what the option -i means and what should be its value in this case.
Q&A:
From: CS 591 class email list [mailto:cs591-l@uccs.edu] On Behalf Of Edward Chow
Sent: Sunday, December 05, 2010 3:47 AM
To: CS 591 class email list
Subject: [CS591-l] Re: CS591 HW #5 problem (SOLVED!)
Rod,
From the attached screendump of your fwout,
You have ACCEPT 128.198.60.197 in INPUT chain which allow walrus packet to comes in.
But you forgot to also ACCEPT 128.198.60.197 in OUTPUT chain which allow the “response” of the session from walrus to return back to walrus.
That is the reason you can ping or ssh from walrus
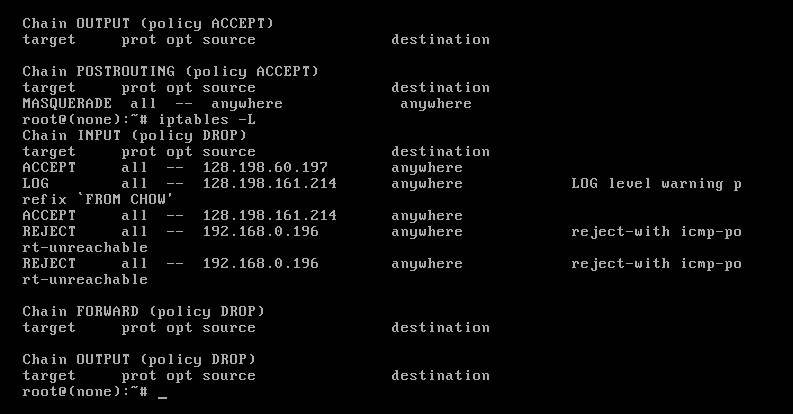
Appear that you are trying to use the laptop at home with 192.168.0.196 as an IP address to test the iptables command with –j REJECT.
It does not work because 192.168.0.0/24 is not a routable IP address. When it goes out from your home gateway, it was changed to an external IP address assigned by your ISP to your internet connection, similar to our DNAT service. Therefore, you should not use 192.168.0.196.
You need to add
Iptables –I OUTPUT 1 –d 128.198.60.197 –j ACCEPT
Note that in the above command, we specifies –d (not –s) since this chain governs the packet from fwout to walrus (the destination IP address contains 128.198.60.197)
I first use –s 128.198.60.197 and was not able to get ping or ssh connected. It is tricky!
After adding the above command, I was able to ping or ssh from walrus to rlykins.csnet.
See the following session data.
[cs591@walrus network-scripts]$ ping rlykins.csnet.uccs.edu
PING rlykins.csnet.uccs.edu (128.198.161.170) 56(84) bytes of data.
^C
--- rlykins.csnet.uccs.edu ping statistics ---
8 packets transmitted, 0 received, 100% packet loss, time 7250ms
You have new mail in /var/spool/mail/cs591
[cs591@walrus network-scripts]$ ssh -l csnet 128.198.161.170
ssh: connect to host 128.198.161.170 port 22: Connection timed out
[cs591@walrus network-scripts]$ ping rlykins.csnet.uccs.edu
PING rlykins.csnet.uccs.edu (128.198.161.170) 56(84) bytes of data.
64 bytes from 128.198.161.170: icmp_seq=1 ttl=62 time=0.969 ms
64 bytes from 128.198.161.170: icmp_seq=2 ttl=62 time=0.506 ms
^C
--- rlykins.csnet.uccs.edu ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1758ms
rtt min/avg/max/mdev = 0.506/0.737/0.969/0.233 ms
[cs591@walrus network-scripts]$ ssh -l csnet 128.198.161.170
The authenticity of host '128.198.161.170 (128.198.161.170)' can't be established.
RSA key fingerprint is 21:47:18:a6:3b:81:c0:3c:fa:ab:08:71:1d:ab:f7:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '128.198.161.170' (RSA) to the list of known hosts.
csnet@128.198.161.170's password:
Linux (none) 2.6.35-22-generic-pae #33-Ubuntu SMP Sun Sep 19 22:14:14 UTC 2010 i686 GNU/Linux
Ubuntu 10.10
Welcome to Ubuntu!
* Documentation: https://help.ubuntu.com/
Last login: Tue Nov 30 20:57:58 2010
csnet@(none):~$
To make it easier for you and your classmates to debug, I just created accounts on chow.csnet.uccs.edu (128.198.161.214) running FC14.
Same password as walrus. #a followed by SID without dash. Note that walrus and chow.csnet does not share file content.
You can add –j LOG command to log, then use –j DROP command to drop those from chow.csnet.
After adding iptables –I INPUT 3 ! –s 128.198.0.0/16 –j LOG –log-prefix ‘from HOME?’ to rlykins_fwout, I ping it from home .
I did not receive any response (tell me why?) but I did see it left the following log records on /var/log/messages of your fwout:
Dec 1 08:59:59 (none) kernel: [43344.794700] from HOME?IN=eth1 OUT= MAC=ff:ff:ff:ff:ff:ff:00:50:56:9b:01:80:08:00 SRC=0.0.0.0 DST=255.255.255.255 LEN=328 TOS=0x10 PREC=0x00 TTL=128 ID=0 PROTO=UDP SPT=68 DPT=67 LEN=308
Dec 1 09:00:07 (none) kernel: [43352.791089] from HOME?IN=eth1 OUT= MAC=ff:ff:ff:ff:ff:ff:00:50:56:9b:01:80:08:00 SRC=0.0.0.0 DST=255.255.255.255 LEN=328 TOS=0x10 PREC=0x00 TTL=128 ID=0 PROTO=UDP SPT=68 DPT=67 LEN=308
Dec 1 09:00:07 (none) kernel: [43352.791106] from HOME?IN=eth1 OUT= MAC=ff:ff:ff:ff:ff:ff:00:50:56:9b:01:80:08:00 SRC=0.0.0.0 DST=255.255.255.255 LEN=328 TOS=0x10 PREC=0x00 TTL=128 ID=0 PROTO=UDP SPT=68 DPT=67 LEN=308
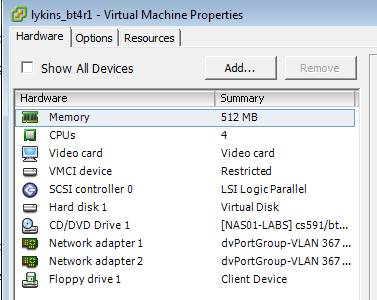
For the bt4r1 problem, you did not change network adapter 1 or 2 to 24-bit block dswitch and turn on “connected” or “connect at power on”.
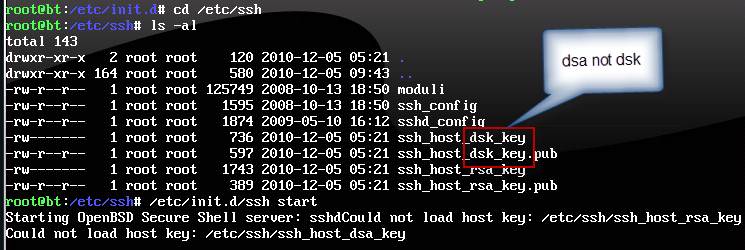
I found I have a typo in ssh-keygen instruction for dsa key,
It should be
ssh-keygen -t dsa -f /etc/ssh/ssh_host_dsa_key
^ a not k (see the error in the above capture filenames
I am not sure if you have generated the key with protected pass-phrase (we should not do that).
I regenerated the two keys and /etc/init.d/ssh start and that works.
The following are session captured to illustrate Step 6 with access from fwin to bt4r1.
Note that we need to add 172.16.170.0/24 and 10.0.170.0/24 into the allowed subnet in INPUT and OUTPUT chains.
I also set the root password on bt4r1 to our typical vm password.
Here we start from a ssh terminal session to fwout.
root@(none):/var/log# ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:9b:01:74
inet addr:128.198.161.170 Bcast:128.198.161.191 Mask:255.255.255.224
inet6 addr: fe80::250:56ff:fe9b:174/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:28015 errors:0 dropped:0 overruns:0 frame:0
TX packets:1363 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3547115 (3.5 MB) TX bytes:155963 (155.9 KB)
Interrupt:18 Base address:0x2000
eth0:1 Link encap:Ethernet HWaddr 00:50:56:9b:01:74
inet addr:128.198.161.171 Bcast:128.198.161.191 Mask:255.255.255.224
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Interrupt:18 Base address:0x2000
eth1 Link encap:Ethernet HWaddr 00:50:56:9b:01:75
inet addr:172.16.170.1 Bcast:172.16.170.255 Mask:255.255.255.0
inet6 addr: fe80::250:56ff:fe9b:175/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3702 errors:0 dropped:0 overruns:0 frame:0
TX packets:1321 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:649145 (649.1 KB) TX bytes:1510714 (1.5 MB)
Interrupt:19 Base address:0x2080
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
root@(none):/var/log# ping 172.16.170.1
PING 172.16.170.1 (172.16.170.1) 56(84) bytes of data.
ping: sendmsg: Operation not permitted
ping: sendmsg: Operation not permitted
ping: sendmsg: Operation not permitted
ping: sendmsg: Operation not permitted
ping: sendmsg: Operation not permitted
^C
--- 172.16.170.1 ping statistics ---
5 packets transmitted, 0 received, 100% packet loss, time 4032ms
root@(none):/var/log# iptables -A INPUT -s 172.16.170.0/24 -j ACCEPT
root@(none):/var/log# iptables -A OUTPUT -d 172.16.170.0/24 -j ACCEPT
root@(none):/var/log# iptables -A INPUT -s 10.0.170.0/24 -j ACCEPT
root@(none):/var/log# iptables -A OUTPUT -d 10.0.170.0/24 -j ACCEPT
root@(none):/var/log# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
128.198.161.160 0.0.0.0 255.255.255.224 U 0 0 0 eth0
172.16.170.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
10.0.170.0 172.16.170.3 255.255.255.0 UG 0 0 0 eth1
10.0.0.0 172.16.170.3 255.0.0.0 UG 0 0 0 eth1
0.0.0.0 128.198.161.161 0.0.0.0 UG 0 0 0 eth0
0.0.0.0 128.198.161.161 0.0.0.0 UG 0 0 0 eth0
root@(none):/var/log# route del -net 10.0.00 gw 172.16.170.3
SIOCDELRT: Invalid argument
root@(none):/var/log# route del -net 10.0.0.0/8 gw 172.16.170.3
root@(none):/var/log# ping 172.16.170.3
PING 172.16.170.3 (172.16.170.3) 56(84) bytes of data.
64 bytes from 172.16.170.3: icmp_req=1 ttl=64 time=3.53 ms
64 bytes from 172.16.170.3: icmp_req=2 ttl=64 time=0.530 ms
^C
--- 172.16.170.3 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1001ms
rtt min/avg/max/mdev = 0.530/2.033/3.537/1.504 ms
root@(none):/var/log# ssh -l csnet 172.16.170.3
The authenticity of host '172.16.170.3 (172.16.170.3)' can't be established.
RSA key fingerprint is 21:47:18:a6:3b:81:c0:3c:fa:ab:08:71:1d:ab:f7:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.170.3' (RSA) to the list of known hosts.
csnet@172.16.170.3's password:
Linux (none) 2.6.35-22-generic-pae #33-Ubuntu SMP Sun Sep 19 22:14:14 UTC 2010 i686 GNU/Linux
Ubuntu 10.10
Welcome to Ubuntu!
* Documentation: https://help.ubuntu.com/
Last login: Tue Nov 30 21:25:08 2010
csnet@(none):~$ sudo hostname fwin
^C
sudo: unable to resolve host (none)
[sudo] password for csnet:
csnet@(none):~$ ping -c 1 10.0.170.4
PING 10.0.170.4 (10.0.170.4) 56(84) bytes of data.
64 bytes from 10.0.170.4: icmp_req=1 ttl=64 time=1.79 ms
--- 10.0.170.4 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 1.799/1.799/1.799/0.000 ms
csnet@(none):~$ ssh -l csnet 10.0.172.4
ssh: connect to host 10.0.172.4 port 22: Connection timed out
csnet@(none):~$ ssh -l root 10.0.170.4
The authenticity of host '10.0.170.4 (10.0.170.4)' can't be established.
RSA key fingerprint is 23:5c:b4:38:66:68:dd:32:ff:2d:1b:8c:44:05:26:37.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '10.0.170.4' (RSA) to the list of known hosts.
root@10.0.170.4's password:
Connection closed by 10.0.170.4
csnet@(none):~$ ssh -l root 10.0.170.4
root@10.0.170.4's password:
Permission denied, please try again.
root@10.0.170.4's password:
Permission denied, please try again.
root@10.0.170.4's password:
Permission denied (publickey,password).
csnet@(none):~$ ssh -l root 10.0.170.4
root@10.0.170.4's password:
Permission denied, please try again.
root@10.0.170.4's password:
Permission denied, please try again.
root@10.0.170.4's password:
Permission denied (publickey,password).
csnet@(none):~$ ssh -l root 10.0.170.4
root@10.0.170.4's password:
Permission denied, please try again.
root@10.0.170.4's password:
BackTrack 4 R1 (PwnSauce Revolution)
root@bt:~#
Edward